I’ll just briefly write about IKE and ISAKMP from theory side, you can always dig up more on the internet. I’ve also written more theory on IPsec on my old blog post regarding IPsec between Sonicwall-Mikrotik. Internet Security Association Key Management Protocol (ISAKMP) is a framework for authentication and key exchange between two peers to establish, modify, and tear down SAs. It is designed to support many different kinds of key exchanges. ISAKMP uses UDP port 500 for communication between peers.
IKE is the implementation of ISAKMP using the Oakley and Skeme key exchange techniques. Oakley provides perfect forward secrecy (PFS) for keys, identity protection, and authentication; Skeme provides anonymity, repudiability, and quick key refreshment.
In Cisco world ISAKMP is the same as IKE. So don’t let that confuse you.
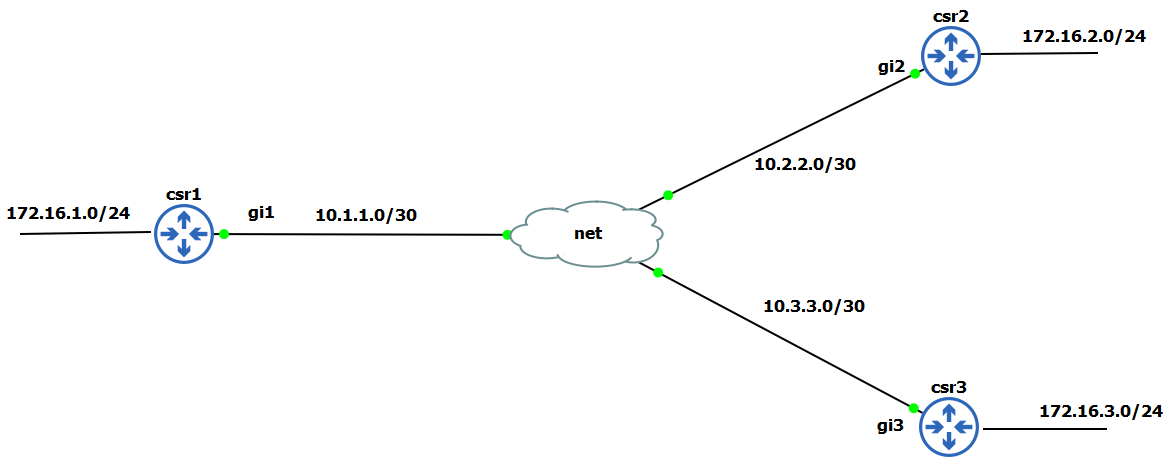
Topology is straightforward and simple so let’s start with configuration. We will use IOS-XE platform.
Steps we take:
First we have to define the isakmp/ike policy which serves so two peers can agree on parameters for encrypting and hashing their key exchange. This is also called IKE Phase 1 Tunnel. And those parameters on which two peers agree are called SA – Security Associations.
Phase 1 Tunnel is used so we can securely bring up the second tunnel which is called IKE Phase 2 Tunnel and with it we can secure and encrypt user’s data transiting over the tunnel.
After defining the policy parameters, we have to define the key and the peer address for which this key is used to establish peering. Adress 0.0.0.0 means that we accept any peer that has the key “test” we defined.
To bring up the Phase 2 Tunnel we also need SA parameters on which two peers agree. They are configured under the IPsec Transform Set, you can choose encryption and hashing which works best for your needs. Under the Transform Set you also define the mode your IPsec tunnel will use.
Tunnel Mode - is the default mode. It use mostly in configuring Site-to-Site IPsec VPNs when there’s no other tunneling mechanisms in use for traffic transit like GRE tunnel. Tunnel Mode encrypts the entire original IP packet and adds a new IP header. Tunnel mode is also mostly used when the original destination of a packet (which is hidden and encrypted inside the original IP header) is different then the destination point which we use to reach the final destination (some private address for example).
Transport Mode - encrypts only the data portion (payload) of each packet and leaves the packet header untouched. Mainly used when you already have some mechanism of encapsulating the inner traffic into the tunnel like GRE. You will mostly use Transport Mode with GRE tunnel, when you want to use Routing Protocols because they need multicast to work. IPsec in tunnel mode doesn’t support multicast.
Finally you have to create ACL’s which define the „interesting“ traffic, meaning the traffic that we want to encrypt and send across the tunnel, and attach it to Crypto Map, which later get’s attached to the interface which creates the tunnel.
It is assumed you have IP reachability with the peer you’re trying to establish the tunnel. In my case i have default route to the “internet”.
csr1 (hub)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
csr1(config)#int gi1
csr1(config-if)#ip add 10.1.1.2 255.255.255.252
csr1(config-if)#no shut
csr1(config-if)#int l0
csr1(config-if)#ip add 172.16.1.1 255.255.255.0
-----------------------------------------------------------------
csr1(config)#crypto isakmp policy 10
csr1(config-isakmp)#encryption aes 256
csr1(config-isakmp)#hash sha256
csr1(config-isakmp)#authentication pre-share
csr1(config-isakmp)#group 5
----------------------------------------------------------------
csr1(config)#crypto isakmp key test address 0.0.0.0
csr1(config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr1(cfg-crypto-trans)#mode tunnel
----------------------------------------------------------------
csr1(config)#crypto map CRYMAP 10 ipsec-isakmp
csr1(config-crypto-map)# set peer 10.2.2.2
csr1(config-crypto-map)# set transform-set TSET
csr1(config-crypto-map)# match address CSR1_CSR2_VPN
csr1(config)#crypto map CRYMAP 20 ipsec-isakmp
csr1(config-crypto-map)# set peer 10.3.3.2
csr1(config-crypto-map)# set transform-set TSET
csr1(config-crypto-map)# match address CSR1_CSR3_VPN
----------------------------------------------------------------
csr1(config)#ip access-list extended CSR1_CSR2_VPN
csr1(config-ext-nacl)#permit ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
csr1(config)#ip access-list extended CSR1_CSR3_VPN
csr1(config-ext-nacl)#permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
---------------------------------------------------------------
csr1(config)#int gi1
csr1(config-if)#crypto map CRYMAP
csr2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
csr2(config)#int gi2
csr2(config-if)#ip add 10.2.2.2 255.255.255.252
csr2(config-if)#no shut
csr2(config-if)#int l0
csr2(config-if)#ip add 172.16.2.1 255.255.255.0
-----------------------------------------------------------------
csr2(config)#crypto isakmp policy 10
csr2(config-isakmp)#encryption aes 256
csr2(config-isakmp)#hash sha256
csr2(config-isakmp)#authentication pre-share
csr2(config-isakmp)#group 5
----------------------------------------------------------------
csr2(config)#crypto isakmp key test address 10.1.1.2
csr2(config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr2(cfg-crypto-trans)#mode tunnel
----------------------------------------------------------------
csr2(config)#crypto map CRYMAP 10 ipsec-isakmp
csr2(config-crypto-map)# set peer 10.1.1.2
csr2(config-crypto-map)# set transform-set TSET
csr2(config-crypto-map)# match address ACL_VPN
----------------------------------------------------------------
csr2(config)#ip access-list extended ACL_VPN
csr2(config-ext-nacl)#permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
csr3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
csr3(config)#int gi3
csr3(config-if)#ip add 10.3.3.2 255.255.255.252
csr3(config-if)#no shut
csr3(config-if)#int l0
csr3(config-if)#ip add 172.16.3.1 255.255.255.0
-----------------------------------------------------------------
csr3(config)#crypto isakmp policy 10
csr3(config-isakmp)#encryption aes 256
csr3(config-isakmp)#hash sha256
csr3(config-isakmp)#authentication pre-share
csr3(config-isakmp)#group 5
----------------------------------------------------------------
csr3(config)#crypto isakmp key test address 10.1.1.2
csr3(config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr3(cfg-crypto-trans)#mode tunnel
----------------------------------------------------------------
csr3(config)#crypto map CRYMAP 10 ipsec-isakmp
csr3(config-crypto-map)# set peer 10.1.1.2
csr3(config-crypto-map)# set transform-set TSET
csr3(config-crypto-map)# match address ACL_VPN
----------------------------------------------------------------
csr3(config)#ip access-list extended ACL_VPN
csr3(config-ext-nacl)#permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
You can use the debug crypto isakmp or debug crypto ipsec before testing the traffic so you can see the creation of Phase1 and Phase2 Tunnels. Don’t forget to source the traffic with correct LAN interface when you use ping.
Also one more tip: If you’re doing NAT, don’t forget to exclude the LAN ip address range which you want to get encrypted and sent into the tunnel from your NAT config, otherwise traffic would get NAT-ed and wouldn’t hit the ACL, and without hitting the ACL, crypto map would not activate and the traffic won’t be forwarded through the tunnel.
1
csr1#ping 172.16.2.1 source 172.16.1.1
If all is working correctly the ping should succeed and you should see packets being encrypted/decrypted:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PHASE1 Tunnel:
csr1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.2.2.2 10.1.1.2 QM_IDLE 1001 ACTIVE
PHASE2 Tunnel:
csr1#show crypto ipsec sa
interface: GigabitEthernet1
Crypto map tag: CRYMAP, local addr 10.1.1.2
local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.2.0/255.255.255.0/0/0)
current_peer 10.2.2.2 port 500
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
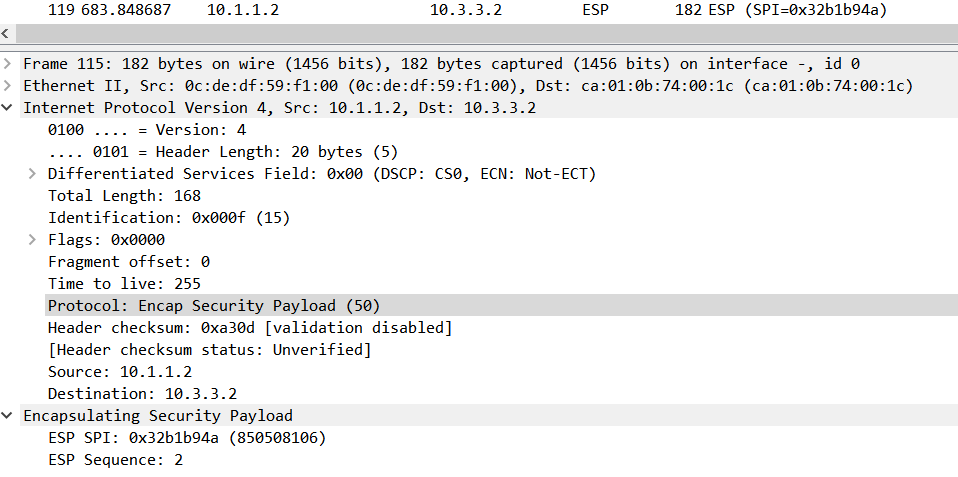
We can see in the traffic capture that the original IP packet is encrypted and you do not see the original source/destination address of our ping. You only see the source/destination of our security endpoints which are used as destinations to reach those networks that are encrypted (our LAN traffic).
Thank you for reading!
