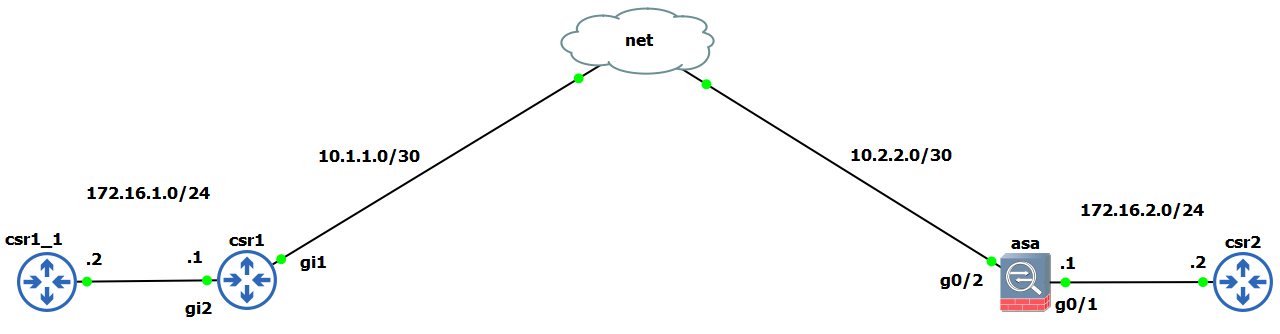
Continuing the IPsec story, this time there will be Router to ASA firewall Crypto Map IPsec configuration. Also we will see how NAT affects the traffic while using IPsec.
csr1_1
1
2
3
csr1(config-if)#int gi2
csr1(config-if)#ip add 172.16.1.2 255.255.255.0
csr1(config-if)#no shut
csr1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
csr1(config)#int gi1
csr1(config-if)#ip add 10.1.1.2 255.255.255.252
csr1(config-if)#no shut
csr1(config-if)#int gi2
csr1(config-if)#ip add 172.16.1.1 255.255.255.0
-----------------------------------------------------------------
csr1(config)#crypto isakmp policy 10
csr1(config-isakmp)#encryption aes 256
csr1(config-isakmp)#hash sha
csr1(config-isakmp)#authentication pre-share
csr1(config-isakmp)#group 5
----------------------------------------------------------------
csr1(config)#crypto isakmp key test address 0.0.0.0
csr1(config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr1(cfg-crypto-trans)#mode tunnel
----------------------------------------------------------------
csr1(config)#crypto map CRYMAP 10 ipsec-isakmp
csr1(config-crypto-map)# set peer 10.2.2.2
csr1(config-crypto-map)# set transform-set TSET
csr1(config-crypto-map)# match address CSR1_ASA_VPN
----------------------------------------------------------------
csr1(config)#ip access-list extended CSR1_ASA_VPN
csr1(config-ext-nacl)#permit ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
---------------------------------------------------------------
csr1(config)#int gi1
csr1(config-if)#crypto map CRYMAP
asa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
asa# conf t
asa(config-if)# int g0/2
asa(config-if)# ip add 10.2.2.2 255.255.255.252
asa(config-if)# nameif outside
asa(config-if)# int g0/1
asa(config-if)# ip add 172.16.2.1 255.255.255.0
asa(config-if)# nameif inside
----------------------------------------------------------------
asa(config)# crypto ikev1 policy 10
asa(config-ikev1-policy)# authentication pre-share
asa(config-ikev1-policy)# encryption aes-256
asa(config-ikev1-policy)# hash sha
asa(config-ikev1-policy)# group 5
---------------------------------------------------------------
asa(config)# crypto ikev1 enable outside
---------------------------------------------------------------
asa(config)# crypto ipsec ikev1 transform-set TSET esp-aes-256 esp-sha-hmac
asa(config)# tunnel-group 10.1.1.2 type ipsec-l2l
asa(config)# tunnel-group 10.1.1.2 ipsec-attributes
asa(config-tunnel-ipsec)# ikev1 pre-shared-key test
---------------------------------------------------------------
asa(config)# access-list ACL_VPN extended permit ip 172.16.2.0 255.255.255.0 172.16.1.0 255.255.255.0
---------------------------------------------------------------
asa(config)# crypto map CRYMAP 10 match address ACL_VPN
asa(config)# crypto map CRYMAP 10 set peer 10.1.1.2
asa(config)# crypto map CRYMAP 10 set ikev1 transform-set TSET
asa(config)# crypto map CRYMAP interface outside
ASA configuration is alittle bit different than IOS.
1.Define the IKEv1 policy which is called ISAKMP on router, we mentioned why in previous blog post.
2.Enable IKE on the proper interface where the tunnel will be established.
3.Define Transform Set same like on IOS.
4.Configure proper tunnel-group type (IPsec LAN-to-LAN tunnel group). Tunnel group contains different connection policies required to set up the tunnel, like preshared key.
5.Match the interesting traffic with the ACL and apply it to crypto map which gets applied to interface via global config.
NOTE: LAN-to-LAN tunnel groups that have names that are not IP addresses can be used only if the tunnel authentication method is Digital Certificates and/or the peer is configured to use Aggressive Mode.
Test from csr2 which is just connected via p2p link with asa.
1
2
3
csr2#ping 172.16.1.1
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
.!!!!
Verify that both tunnels are active:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
asa# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 10.1.1.2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
-----------------------------------------------------------------------------------------------------
asa# show crypto ipsec sa
interface: outside
Crypto map tag: CRYMAP, seq num: 10, local addr: 10.2.2.2
access-list ACL_VPN extended permit ip 172.16.2.0 255.255.255.0 172.16.1.0 255.255.255.0
local ident (addr/mask/prot/port): (172.16.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
current_peer: 10.1.1.2
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
The tunnel’s are up and ping went through successfully. That’s the basics of IPsec , now we will complicate it a little bit and we will see what happens when NAT is used and how we need to be careful on matching the correct traffic.
csr1 NAT config
1
2
3
4
5
6
7
csr1(config)#int gi1
csr1(config-if)#ip nat outside
csr1(config-if)#int gi2
csr1(config-if)#ip nat inside
csr1(config)#ip access-list extended NAT_VPN
csr1(config-ext-nacl)#permit ip 172.16.1.0 0.0.0.255 any
csr1(config)#ip nat inside source list NAT_VPN interface GigabitEthernet1 overload
Now if we try to ping from csr1_1 (172.16.1.2) to csr2 (172.16.2.2) we get unreachable message:
1
2
3
csr1_1#ping 172.16.2.2
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
UUUUU
This is happening because once the traffic comes into csr1, the flow of operation goes like this: Routing first, and then NAT before the crypto-map.
That means that csr1 will send traffic for 172.16.2.2 towards default gateway to the internet, and that traffic would get NAT-ed because we’ve configured the ACL NAT_VPN to match on all traffic which comes from 172.16.1.0 and going anywhere.
So traffic would match the wrong ACL and it wouldn’t pass through the ipsec tunnel.
We can verify by looking at the NAT translation on csr1:
1
2
3
csr1#show ip nat trans
Pro Inside global Inside local Outside local Outside global
icmp 10.1.1.2:7 172.16.1.2:7 172.16.2.2:7 172.16.2.2:7
To fix this, we have to edit the NAT_VPN ACL to deny the 172.16.1.0/24 range from NAT-ing when going towards the 172.16.2.0/24 network. And the rule has to be above the previous one.
1
2
3
4
5
6
7
csr1(config)#ip access-list extended NAT_VPN
csr1(config-ext-nacl)#5 deny ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
-----------------------------------------------
csr1#show ip access-list
Extended IP access list NAT_VPN
5 deny ip 172.16.1.0 0.0.0.255 172.16.2.0 0.0.0.255
10 permit ip 172.16.1.0 0.0.0.255 any
Now we can check if the ping works:
1
2
3
4
5
csr1_1#ping 172.16.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 12/24/32 ms
The ping is successful, and the traffic is matching the tunnel ACL and it is not NATing to outside, but instead it is passing through the tunnel towards the destination.
Let’s do the same on ASA:
asa NAT config
1
2
3
asa(config)# object network net_172.16.2.0
asa(config-network-object)# subnet 172.16.2.0 255.255.255.0
asa(config-network-object)# nat (inside,outside) dynamic interface
This is Section 2 NAT configured under the object, also called Auto-NAT and basically it is PAT on the outside interface.
When we try to ping from csr2 (172.16.2.2) to csr1_1 (172.16.1.2) the ping fails because the traffic is getting NAT-ed.
1
2
3
4
csr2#ping 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
.....
1
2
3
4
5
6
asa# show xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
ICMP PAT from inside:172.16.2.2/2 to outside:10.2.2.2/2
Now we need to do NAT exemption just like we did on csr1 for the traffic going to the remote location. On ASA we configure it a little differently and it is called Twice NAT.
1
2
3
4
5
asa(config)# object network LOCAL_172.16.2.0
asa(config-network-object)# subnet 172.16.2.0 255.255.255.0
asa(config)# object network REMOTE_172.16.1.0
asa(config-network-object)# subnet 172.16.1.0 255.255.255.0
asa(config)# nat (inside,outside) source static LOCAL_172.16.2.0 LOCAL_172.16.2.0 destination static REMOTE_172.16.1.0 REMOTE_172.16.1.0
What we did here is we created an object for local and remote networks, and we’ve created NAT rule which belong to Section1 (Manual NAT). Section1 is preferred over Section2 (Auto NAT which we did before).
This means all traffic coming from inside to outside which has an address in 172.16.2.0/24 range, NAT to itself (or no NAT) when it is going to the destination network 172.16.1.0/24 which also stays itself and doesn’t NAT to other network.
All other traffic will fall to Section2 rule which will NAT traffic when it is going to other destination not specified in our Section1 rule.
This way the ACL we’ve created for the traffic which is supposed to be pushed through the tunnel will get matched.
1
2
3
4
5
6
7
8
asa(config)# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static LOCAL_172.16.2.0 LOCAL_172.16.2.0 destination static REMOTE_172.16.1.0 REMOTE_172.16.1.0
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (inside) to (outside) source dynamic net_172.16.2.0 interface
translate_hits = 2, untranslate_hits = 10
Now when we try the ping it works:
1
2
3
4
5
csr2#ping 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/39/60 ms
And we check NAT on asa and see that it is matching the proper rule in Section1, and the traffic is not getting NATed.
1
2
3
4
5
6
7
8
asa# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static LOCAL_172.16.2.0 LOCAL_172.16.2.0 destination static REMOTE_172.16.1.0 REMOTE_172.16.1.0
translate_hits = 2, untranslate_hits = 2
Auto NAT Policies (Section 2)
1 (inside) to (outside) source dynamic net_172.16.2.0 interface
translate_hits = 2, untranslate_hits = 10
Verify that it is static Twice NAT by flag “sIT”.
1
2
3
4
5
6
7
8
asa# show xlate
2 in use, 2 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from inside:172.16.2.0/24 to outside:172.16.2.0/24
flags sIT idle 0:12:01 timeout 0:00:00
NAT from outside:172.16.1.0/24 to inside:172.16.1.0/24
flags sIT idle 0:12:01 timeout 0:00:00
And also we can see the ACL hits:
1
2
asa# show access-list
access-list ACL_VPN line 1 extended permit ip 172.16.2.0 255.255.255.0 172.16.1.0 255.255.255.0 (hitcnt=6)
Additionally we can also verify on asa if packets are encrypted/decrypted:
1
2
3
4
5
asa# show crypto ipsec sa | i pkts
#pkts encaps: 15, #pkts encrypt: 15, #pkts digest: 15
#pkts decaps: 22, #pkts decrypt: 22, #pkts verify: 22
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 15, #pkts comp failed: 0, #pkts decomp failed: 0
Thank you for reading!
