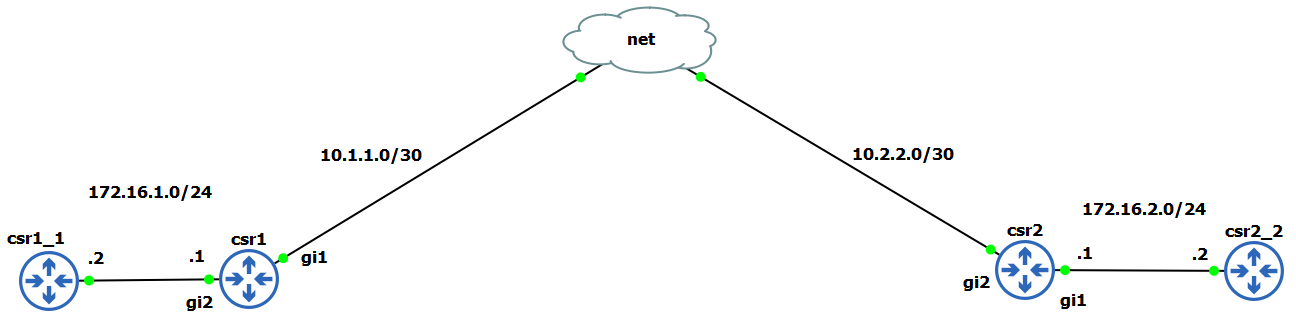
GRE (Generic Routing Encapsulation) is tunneling mechanism which uses IP for transport and it can encapsulate and carry other protocols over the tunnel. The tunnels are like p2p links. For example IPsec alone can’t carry routing protocols and doesn’t support multicast. That is why GRE is used for transport and IPsec for protection of the traffic.
Here we will see both ways of configuring GRE over IPsec with Crypto Map and with IPsec Profile.
GRE over IPsec Using Crypto Map
First we bring up the GRE tunnel and verify connectivity:
1
2
3
4
5
6
7
8
9
csr1(config)#int tun0
csr1(config-if)#ip address 50.0.0.1 255.255.255.0
csr1(config-if)#tunnel source gi1
csr1(config-if)#tunnel destination 10.2.2.2
------------------------------------------------------------
csr2(config)#int tun0
csr2(config-if)#ip address 50.0.0.2 255.255.255.0
csr2(config-if)#tunnel source gi2
csr2(config-if)#tunnel destination 10.1.1.2
1
2
3
4
5
6
7
8
9
10
11
12
csr1#show ip int br
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 10.1.1.2 YES NVRAM up up
GigabitEthernet2 172.16.1.1 YES NVRAM up up
GigabitEthernet3 unassigned YES NVRAM administratively down down
GigabitEthernet4 unassigned YES NVRAM administratively down down
Tunnel0 50.0.0.1 YES manual up up
csr1#ping 50.0.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 50.0.0.2, timeout is 2 seconds:
!!!!!
We can see tunnel is up and reachable.
Now we configure IPsec to protect the traffic:
csr1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
csr1(config)#crypto isakmp policy 10
csr1(config-isakmp)# encr aes 256
csr1(config-isakmp)# hash sha256
csr1(config-isakmp)# authentication pre-share
csr1(config-isakmp)# group 5
----------------------------------------------
csr1(config)#crypto isakmp key test address 10.2.2.2
----------------------------------------------
csr1(config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr1(cfg-crypto-trans)# mode transport
----------------------------------------------
csr1(config)#ip access-list extended GRE_ANY
csr1(config-ext-nacl)#permit gre any any
----------------------------------------------
csr1(config)#crypto map CRYMAP 10 ipsec-isakmp
csr1(config-crypto-map)# set peer 10.2.2.2
csr1(config-crypto-map)# set transform-set TSET
csr1(config-crypto-map)# match address GRE_ANY
----------------------------------------------
csr1(config)#int gi1
csr1(config-if)#crypto map CRYMAP
csr2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
csr2 (config)#crypto isakmp policy 10
csr2 (config-isakmp)# encr aes 256
csr2 (config-isakmp)# hash sha256
csr2(config-isakmp)# authentication pre-share
csr2 (config-isakmp)# group 5
----------------------------------------------
csr2 (config)#crypto isakmp key test address 10.1.1.2
----------------------------------------------
csr2 (config)#crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
csr2 (cfg-crypto-trans)# mode transport
----------------------------------------------
csr2 (config)#ip access-list extended GRE_ANY
csr2 (config-ext-nacl)#permit gre any any
----------------------------------------------
csr2 (config)#crypto map CRYMAP 10 ipsec-isakmp
csr2 (config-crypto-map)# set peer 10.1.1.2
csr2 (config-crypto-map)# set transform-set TSET
csr2 (config-crypto-map)# match address GRE_ANY
----------------------------------------------
csr2 (config)#int gi2
csr2 (config-if)#crypto map CRYMAP
Everything is the same like regular IPsec configuration except that here we change the ACL to match on all traffic entering the GRE tunnel, meaning all traffic that is permitted to enter the GRE tunnel is also encrypted by IPsec.
Also now we are using the transport mode instead of the tunnel mode like we used for pure IPsec tunnel.
Tunnel Mode in IPsec usually implies traffic from inside interfaces on both sides being encrypted and tunneled through. There is no IP addressing in tunneling mode, ESP header is sitting behind IP header (public ip) so it knows to which endpoint to talk to and encrypting traffic.
Transport is different because it doesn’t tunnel the traffic from inside to inside, the router or device doing IPsec is terminating the traffic itself on the outer interface and is routed to other interface.So it is like an outside tunnel on which we can do routing protocol peerings and advertise routes. In this case Tunnel’s contain IP addressing information. In summary we are not tunneling the traffic with IPsec we are just encrypting it, tunneling is done by GRE.
You still apply crypto map to physical interface.
Now we can do routing protocol peering and advertise routes across the tunnel:
1
2
3
4
5
6
7
csr1(config)#router eigrp 1
csr1(config-router)#network 50.0.0.0
csr1(config-router)#network 172.16.1.0
---------------------------------------------------------
csr2(config)#router eigrp 1
csr2(config-router)#network 50.0.0.0
csr2(config-router)#network 172.16.2.0
We can see the peering is done and the routes are advertised across the tunnel:
1
2
3
4
5
6
7
8
9
csr1#show ip route
S* 0.0.0.0/0 [1/0] via 10.1.1.1
***output removed***
D 172.16.2.0/24 [90/26880256] via 50.0.0.2, Tunnel0
-------------------------------------
csr2#show ip route
S* 0.0.0.0/0 [1/0] via 10.2.2.1
***output removed***
D 172.16.1.0/24 [90/26880256] via 50.0.0.2, Tunnel0
Test reachability, and traceroute to see the traffic going through the tunnel:
1
2
3
4
5
6
7
8
9
10
csr1#ping 172.16.2.2
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 26/28/31 ms
---------------------------------------------------------
csr1#traceroute 172.16.2.2
Tracing the route to 172.16.2.2
VRF info: (vrf in name/id, vrf out name/id)
1 50.0.0.2 17 msec 23 msec 16 msec
2 172.16.2.2 28 msec 16 msec 19 msec
Also check if the traffic is encrypted:
1
2
3
4
5
6
7
8
9
10
11
12
csr1#show crypto ipsec sa
interface: GigabitEthernet1
Crypto map tag: CRYMAP, local addr 10.1.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
current_peer 10.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 407, #pkts encrypt: 407, #pkts digest: 407
#pkts decaps: 408, #pkts decrypt: 408, #pkts verify: 408
We can see the packets are being encrypted/decrypted and we can also see the number of protocol “47” which marks GRE.
Now let’s check the configuration using the IPsec Profile instead of the Crypto map and why it is better and easier method.
GRE over IPsec using IPsec Profile
IPsec Profile offers us cleaner configuration, and much simpler configuration where you map the profile to the tunnel interface. And whatever profile matches will be encrypted. So we don’t need ACLs anymore or the long configuration of crypto map and peers like before.
First we remove the Crypto map configuration from the interface and then we create the profile:
1
2
3
4
5
6
7
8
9
10
11
12
13
csr1(config-if)#int gi1
csr1(config-if)#no crypto map CRYMAP
csr1(config)#crypto ipsec profile IPSEC_PROFILE
csr1(ipsec-profile)#set transform-set TSET
csr1(config)#int tun0
csr1(config-if)#tunnel protection ipsec profile IPSEC_PROFILE
-------------------------------------------------------------
csr2(config-if)#int gi2
csr2(config-if)#no crypto map CRYMAP
csr2(config)#crypto ipsec profile IPSEC_PROFILE
csr2(ipsec-profile)#set transform-set TSET
csr2(config)#int tun0
csr2(config-if)#tunnel protection ipsec profile IPSEC_PROFILE
And that’s it , all other configuration stay the same regarding isakmp policy and transform set we configured before. So the full config would be much cleaner:
1
2
3
4
5
6
7
8
9
10
11
csr1#show run | s crypto
crypto isakmp policy 10
encr aes 256
hash sha256
authentication pre-share
group 5
crypto isakmp key test address 10.2.2.2
crypto ipsec transform-set TSET esp-aes 256 esp-sha-hmac
mode transport
crypto ipsec profile IPSEC_PROFILE
set transform-set TSET
Verifying connectivity:
1
2
3
4
5
6
7
8
9
10
11
12
csr1#ping 172.16.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 30/32/36 ms
--------------------------------------------------------
csr1#traceroute 172.16.2.2
Type escape sequence to abort.
Tracing the route to 172.16.2.2
VRF info: (vrf in name/id, vrf out name/id)
1 50.0.0.2 22 msec 16 msec 20 msec
2 172.16.2.2 20 msec 21 msec 16 msec
One important difference between Crypto map matching and IPsec profile is that with crypto map ACL you were matching all traffic that is protocol 47 (GRE) , and local/remote identity would show 0.0.0.0/0 as address. While now it actually says which local/remote endpoints are to be matched along with protocol number 47 (GRE) and allowed to pass through and be encrypted.
1
2
3
4
5
6
7
8
9
10
11
12
csr1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 10.1.1.2
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.1.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.2.2.2/255.255.255.255/47/0)
current_peer 10.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 193, #pkts encrypt: 193, #pkts digest: 193
#pkts decaps: 191, #pkts decrypt: 191, #pkts verify: 191
Thank you for reading!
